Select Regions and Encryption Key Management System
Before you can use Cohesity Cloud Protection Service, you need to select at least one cloud region for your data backups and choose your desired encryption options for securing your backups.
Once data is backed up to one region, you cannot move it to another. To back your data up in another region, you can add that region and start protecting your data there.
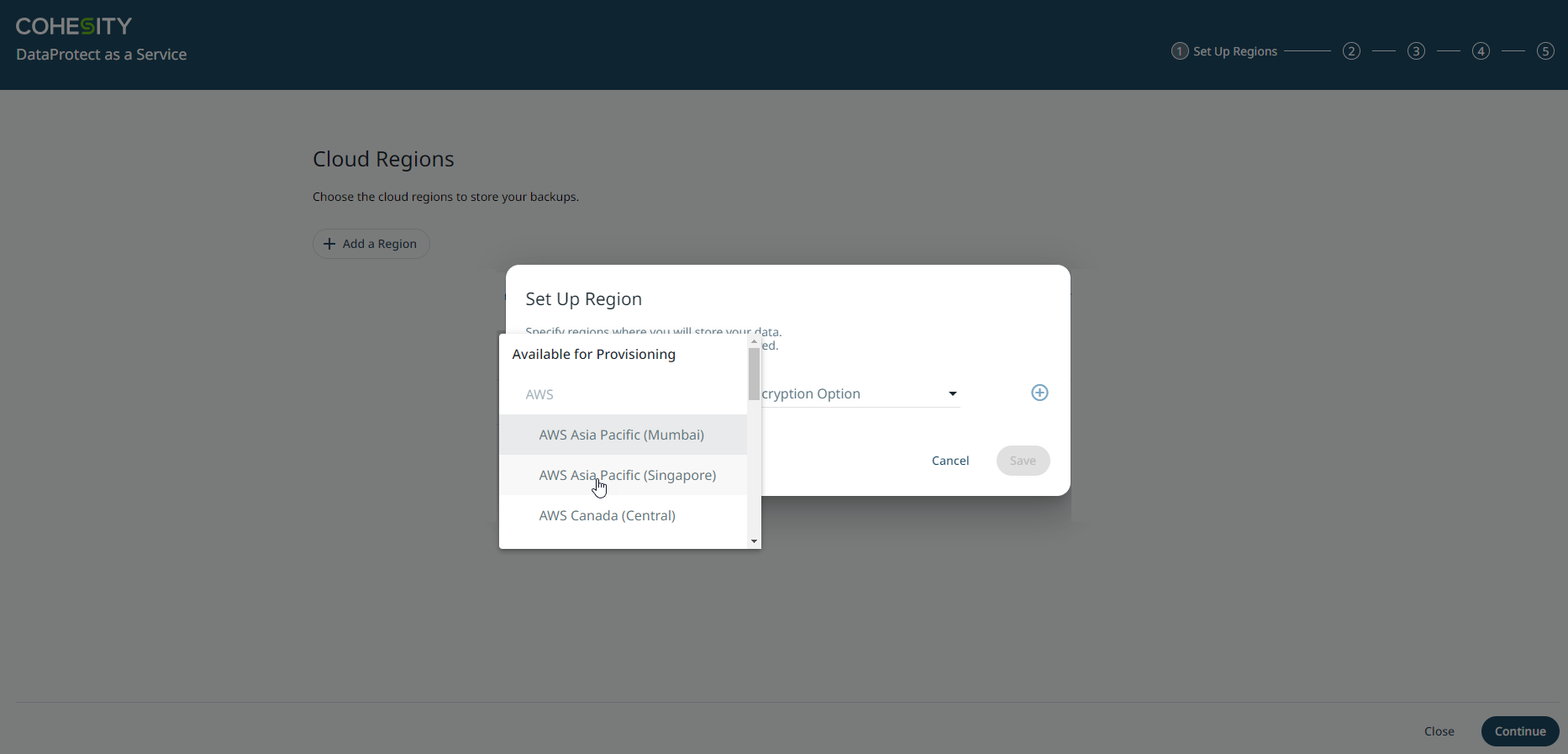
On the Cloud Regions page, click Add a Region.

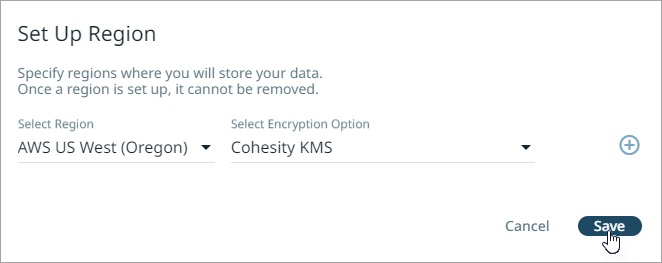
From the Set Up Region dialog, select the cloud region for your data backups and choose the encryption option. For more information on the encryption options, see Choose Key Management System (KMS).
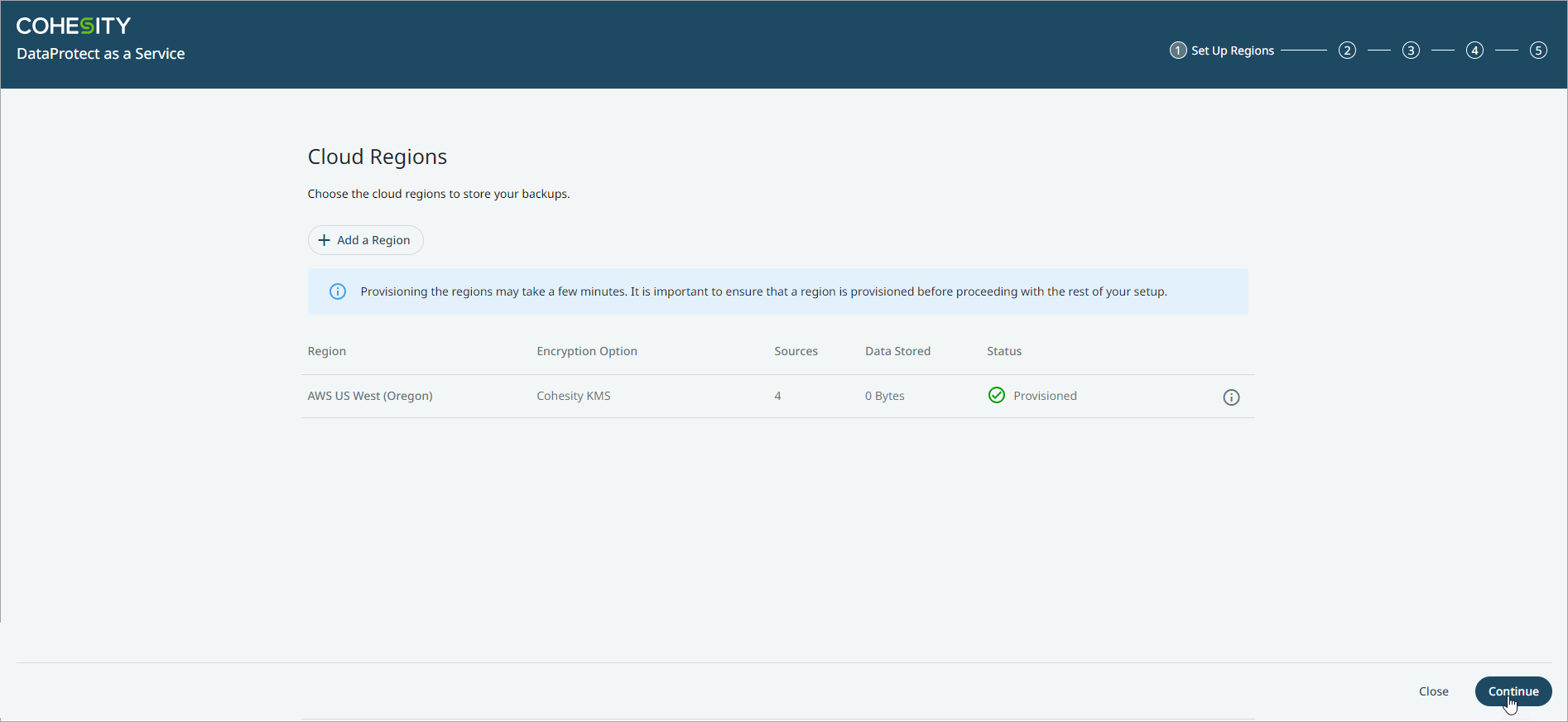
Once the cloud region is provisioned, click Continue.
Choose Key Management System (KMS)
In Cohesity Cloud Protection Service, all the data is encrypted both in flight and at rest. The encryption keys used for at-rest data encryption are the AWS Key Management System (KMS) or Azure Key Vault keys. Customers can choose to encrypt their data using Cohesity-generated AWS KMS or Azure Key Vault keys or bring their own AWS KMS or Azure Vault keys:
Once a cloud region is provisioned with an encryption option, you cannot remove the region and re-provision using a different encryption option.
-
Cohesity KMS. Depending on the region you select to store the data, Cohesity generates and uses unique AWS KMS keys or Azure Key Vault keys for each customer to encrypt their data.
-
Self-Managed KMS. You can also use your own AWS encryption keys (Customer Master Keys) or Azure Key Vault keys.
-
To use your own AWS encryption keys (Customer Master Keys), see Self-Managed KMS for AWS.
-
To use your own Azure Key vault keys, see Self-Managed KMS for Azure.
-
In both encryption options, Cohesity uses AES-256 encryption keys called DEKs (Data Encryption Keys) to encrypt the data at rest. DEKs are generated using the AWS CMK and rotated every 4 hours. The Data Encryption Key is encrypted with the AWS CMK and stored along with the data—it is never stored in plain text.
Next > Add users to access the Cohesity Cloud Protection Service.
