Self-Managed KMS for AWS
To encrypt your data, you can use your own AWS encryption keys (Customer Managed Keys).
Prerequisites
Review and understand the following high level process of using your own AWS encryption keys (Customer Managed Keys):
-
You provide the CMK Amazon Resource Name (ARN) for the cloud region you selected.
Cohesity supports both single and multi region self-managed KMS keys.
-
Cohesity generates the JSON for a key policy document that allows the Cloud Protection Service to make API calls to your CMK.
-
You add the generated JSON contents to your AWS CMK's Policy in your AWS account.
Cohesity recommends using the Cohesity-managed KMS for data encryption. If you choose the self-managed KMS, you are responsible for protecting the CMK keys used for data encryption. Note that if the CMS keys are compromised, then the data stored on Cohesity Cloud Protection Service will not be recoverable.
With the Self-Managed KMS option, you can audit the access calls made to your CMK to find important information, including when the CMK was used, the operation that was requested, the identity of the requester, and the source IP address. For more information, see Logging AWS KMS API calls with AWS CloudTrail and What Is AWS CloudTrail? in the AWS documentation.
Note that you can also revoke CMK access to Cohesity at any time, after which Cohesity cannot decrypt the data stored in Cohesity Cloud Protection Service and all backup & recovery operations will fail.
Configure Self-Managed KMS for AWS
To use your own AWS KMS keys, on the Set Up Region dialog, perform the following:
-
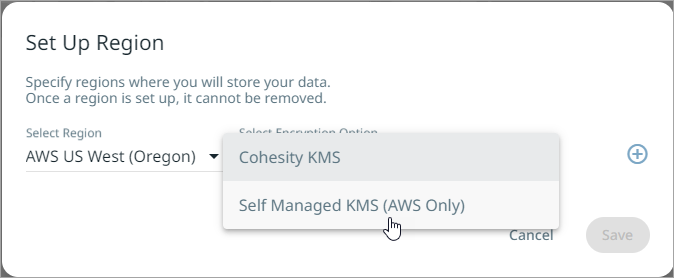
Choose the Region and select the Self Managed KMS (AWS Only) as the Encryption Option.
-
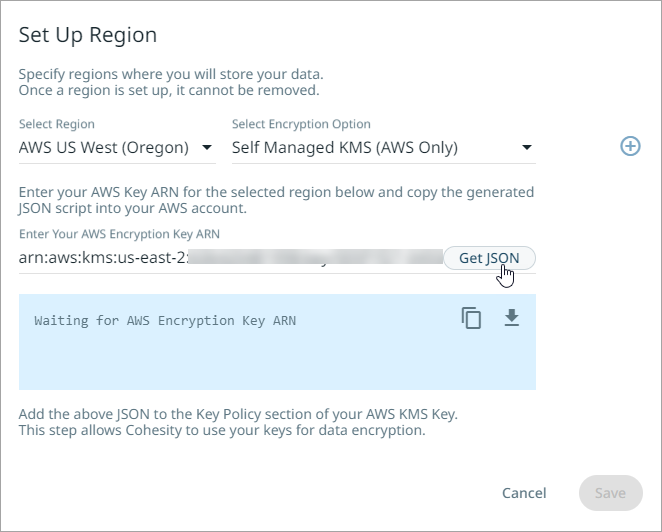
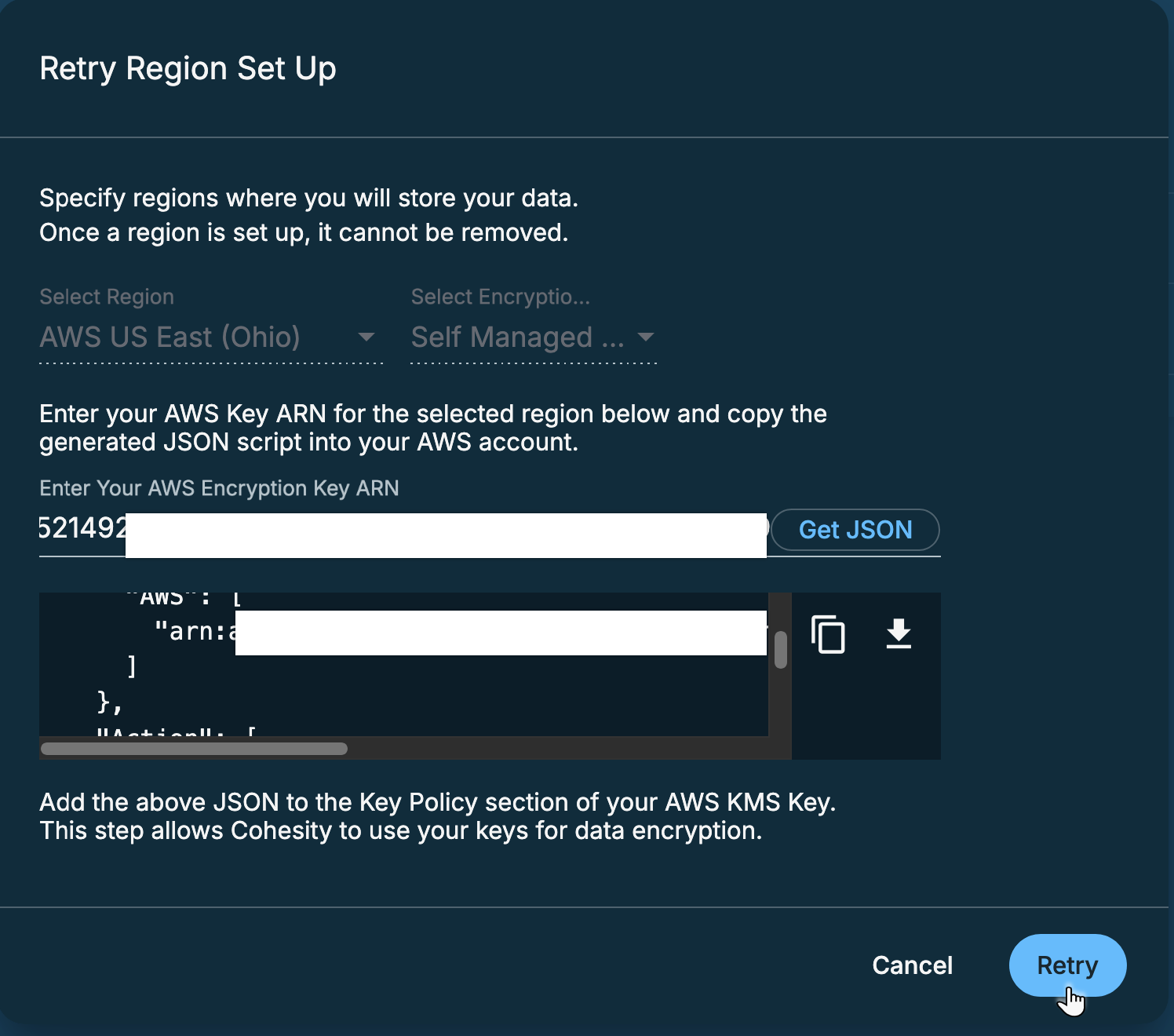
Enter your AWS Key ARN for the selected region and click Get JSON.
-
Copy the generated JSON script.

Go to your AWS CMK and add the copied JSON script under the “Statement” element in the Key Policy section as shown below:

-
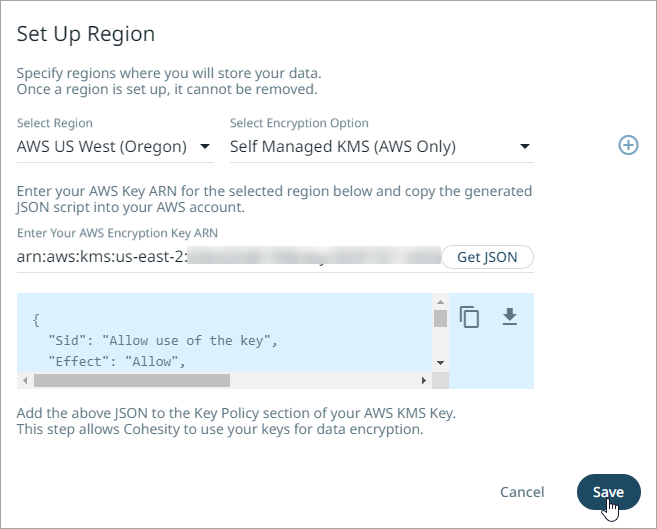
Click Save.
Retry Self-Managed KMS Provisioning for AWS
If the AWS KMS key validation fails due to incorrect or invalid input during the region setup, you can re-enter the correct configuration details and resume the provisioning process without restarting the entire process.
This is a Private Preview feature. Contact your Cohesity account team to enable the feature.
To retry AWS KMS key validation:
-
Click the Actions menu (
 ) next to the Status column and select Review and Retry.
) next to the Status column and select Review and Retry.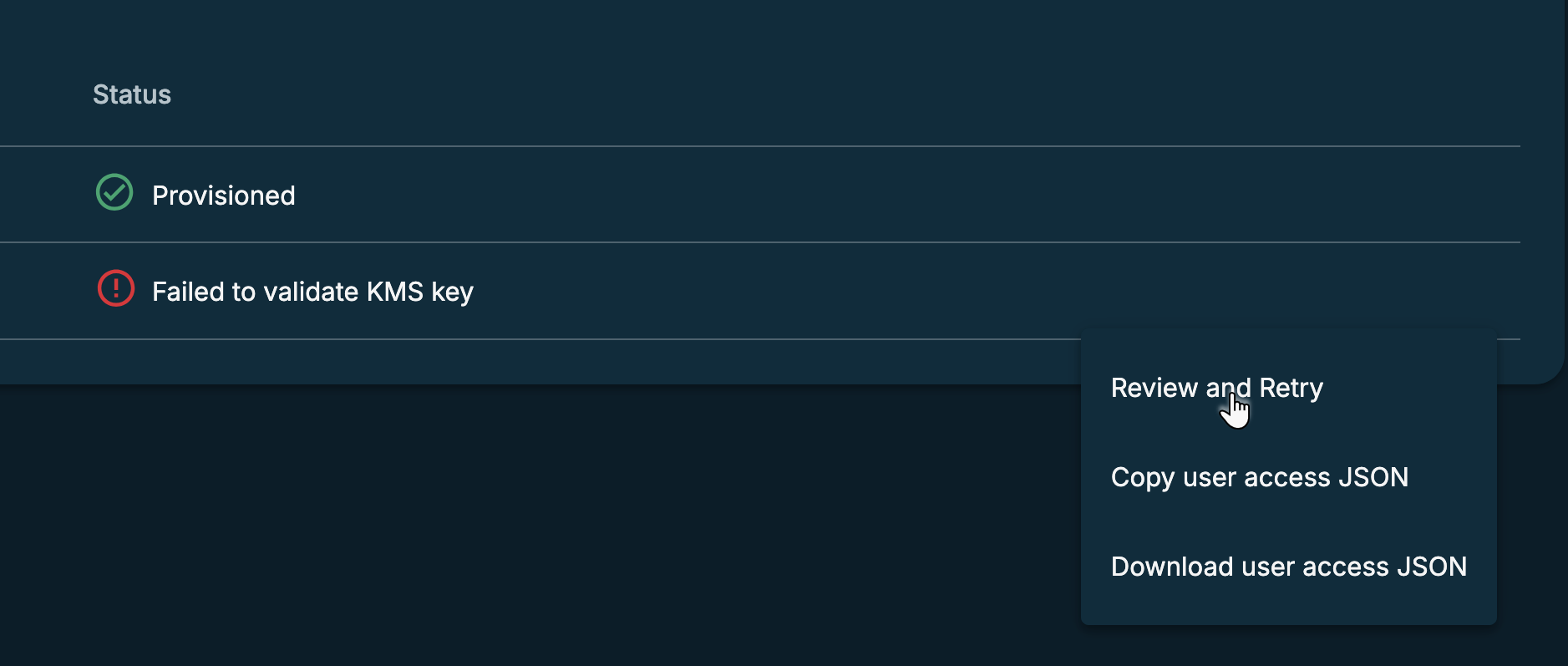
-
On the Retry Region Set Up pop-up screen, verify and update AWS Key ARN for the selected region.
-
Copy the generated JSON script, go to your AWS CMK and add the copied JSON script under the “Statement” element in the Key Policy section.
-
Click Retry to complete the AWS KMS key validation.
Next > Add users to access the Cohesity Cloud Protection Service.
