Protect NAS Sources
Use Cohesity Cloud Protection Service to protect the NAS volumes, files, and folders in your data center. You can protect any generic NAS source, a Dell EMC Isilon NAS cluster, or a NetApp ONTAP cluster or SVM with Cohesity Cloud Protection Service — just note that the registration process is different for each:
Once registered, your NAS source is ready for protection!
Ensure that the TCP/UDP ports 445, 8080, 111, and 2049 are open in the firewall between Cohesity Cloud Protection Service and your NAS device.
Protect NAS
-
In Cloud Protection Service, navigate to Sources, find the NAS source name and click into it.
-
Use the filters and search box at the top to narrow your search.
-
Use the checkboxes to select the objects for protection. To protect the whole source, click the checkbox above the column.
When you check a parent object, you can choose:
-
Select All Child Objects. To capture the tree as it currently exists, or
-
Auto Protect This <NAS source type>. To capture the tree and any future additions.
-
-
Click the Protect icon above the checkboxes.
The New Protection dialog appears.
When setting up protection, you can choose to use either the NFSv3 or NFSv4.1 protocol.
If you select the NFSv4.1 protocol, the option to use the NFSv4.1 protocol for NFS volumes will be enabled in the New Protection dialog under Backup Preferences for NFS Volumes.If the volume supports only NFSv3, the Backup Preference for NFS Volumes option will be hidden.
-
In the New Protection dialog, select a Policy that matches the schedule and retention period you need. If the existing policies do not meet your needs, you can create a new policy with the settings you need.
Cohesity recommends a first full and incremental forever backup approach to protect your NAS sources.
-
To change or configure any of the additional settings , select More Options and perform the below steps or else, click Protect.
-
In the Start Time field, enter the time the protection run should start. The default time zone is the browser's time zone. You can change the time zone of the job by selecting a different time zone.
-
If you need to change any of the additional settings, click the down arrow icon next to Additional Settings and click Edit.
-
Click Protect.
Your selected NAS objects are backed up with the frequency and retention as defined in the policy you have selected.
The backups start immediately after you protect the objects, regardless of the time you set for the protection run.
-
Exclusions and Inclusions: Everything is included by default. Toggle on Exclusions and Inclusions if you want to exclude or include locations. By creating exclusion and inclusion rules, you can limit the Protection Group to a specific set of files and directories and therefore minimize the disk space used to store the data.
To add an exclusion or inclusion, you must prefix a forward slash (‘/’) or suffix an asterisk (‘*’) to the path or to a particular file within the protected object. For example, ‘/test’ or ‘*.txt’.
Add Inclusion: Click to include a particular path or a particular file within the protected object.
For example, consider four directories - test, test1, test2, and test3 under the protected object with path /ifs/TestShare1/Folder1. The table below lists the input types for an inclusion list of folders and their respective outcome:
| Input | Outcome |
|---|---|
| / | Everything inside the protection path is backed up, if exclusions are not defined. |
| /test |
When inclusion path is not suffixed by '/', Protection Group will include all folders starting from protection path. In this example, /test will behave as /test* and Protection Group will include 'test', 'test1', 'test2’, and 'test3' from protection path for backup. |
| /test/ |
When inclusion path is suffixed by '/' , it will only include specific folder. In this example, /test/ behaves as /test/* and Protection Group will only include 'test' from protection path for backup. |
Do not provide the folder name along with the backup path while including files and folders for a Protection Group. The backup path is considered by default. For example, /ifs/TestShare1/Folder1/test does not include any folder.
If exclusions are defined, they will take precedence over inclusions.
Add Exclusion: Click to exclude a particular path or a particular file within the protected object. You can also specify regular expressions for excluding files in the format regex:<regex pattern>
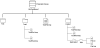
For example, consider there are three directories-Test, Test1, and Folder1 and a file, TestFile.tmp under the protected object with path /ifs/TestShare1.
-
Test1 folder has TestFile1.tmp, TestFile2.tmp files.
-
Folder1 folder has TestFile3.tmp, TestFile4.tmp files, and SubFolder1 which further has a Test folder with File.txt, File1.txt files in it.
The following figure illustrates the directory structure under the protected object with path /ifs/TestShare1.
The table below lists the input types for an exclusion list of folders and their respective outcome:
| Input | Description | Outcome |
|---|---|---|
| /Test |
When the exclusion path is not suffixed by a '/', the Protection Group will exclude all files and folders with Test as the prefix . For exclusions, /Test behaves as /Test*. Exclusion will not be effective on the sub-directory level. |
Excludes Test and Test1 folders, and TestFile1.tmp file from the protection path. TestFile3.tmp and TestFile4.tmp files in the Folder1 folder will not be excluded. |
| /Test/ |
When the exclusion path is suffixed by '/' , the Protection Group excludes only the files and folders with the name Test. For exclusions, /Test/ behaves as /Test/*. Exclusion will not be effective on the sub-directory level. |
Excludes the Test folder of the parent directory. The Test sub-folder in /Folder1/SubFolder1 will not be excluded. |
| */Test |
Excludes all the files and directories with the name 'Test'. Exclusion will be effective on all levels of sub-directories. |
Excludes the Test folder of the parent directory and the Test sub-folder in /Folder1/SubFolder1. |
| *.tmp |
Excludes all the files that with ‘.tmp’. Exclusion will be effective on all levels of sub-directories. |
Excludes TestFile.tmp, TestFile1.tmp, TestFile2.tmp, TestFile3.tmp, TestFile4.tmp files. |
| regex:.*\.tmp |
Excludes the files and folders with ‘.tmp’. Exclusion will be effective on all levels of sub-directories. |
Excludes TestFile.tmp, TestFile1.tmp, TestFile2.tmp, TestFile3.tmp, TestFile4.tmp files. |
| regex:/Folder1/.*/Test/.*\.txt$ |
Excludes all files with .txt extension from all the Test folders directory in /Folder1/.
|
Excludes File.txt and File1.txt files in the /Folder1/SubFolder/Test folder. |
Do not provide the folder name along with the backup path while excluding files and folders for a Protection Group. The backup path is considered by default. For example, /ifs/TestShare1/Folder1/test does not exclude any folder.
Cohesity automatically excludes the following NetApp system files:
- .vtoc_internal and .bplusvtoc_internal files
- .copy-offload directory and .tokens file
Additional Settings
| Additonal Settings | Description |
|---|---|
| End Date |
If you need to end protection on a specific date, enable this to select the date. |
| Skip Files on Errors |
(On by default) A protection run continues even if it encounters errors on files, such as permissions errors. If files are skipped, the protection run details page indicates a Warning status and provides additional information. If toggled off, the protection run stops when it encounters an error. |
| Use Isilon Change Lists |
Toggle on this option to use the vendor-native Change File Tracking (CFT) method for file discovery during an incremental backup. In this method, Cohesity leverages the Isilon CFT API to identify the delta between two snapshot copies. It reduces the time taken to discover the files and folders to backup. If this option is toggled off, Cohesity uses the Cohesity's built-in CFT method. In this method, Cohesity uses its internal File-Runner to discover the delta between two snapshot copies. By default, this option is disabled. Due to the limitations set by Isilon, only one change list can be run at a time. If the Protection Group contains multiple shares to back up, Isilon creates delta for each share serially. |
| Exclusions and Inclusions | By default, all files and folders are included for protection. Use this option if you want to exclude or include specific locations. By creating exclusion and inclusion rules, you can limit the protection to a specific set of files and directories and therefore minimize the disk space used to store the data. |
| Cancel Runs at Quiet Time Start |
(Available only if the selected policy has at least one Quiet Time.) When enabled, all the protection runs that are currently executing will cancel when the Quiet Time period starts. By default, this setting is disabled, meaning that after a protection run starts, it continues to execute even when a Quiet Time period starts. However, new protection runs will not start during a Quiet Time. |
| SLA |
The service-level agreement (SLA) defines how long the administrator expects a protection run to take. Enter:
|
Next > When the first protection run completes, you will be ready to recover NAS volumes, files, and folders when and if you need to.